Companies are getting scammed out of tens of thousands of dollars at a time, and some don’t notice for days and even weeks.
Employers and HR Professionals are often the targets of malicious hacking attempts – usually through suspicious-looking emails that attempt to garner and/or change personal financial information. These scams are known as “business email compromise” (BEC).
More and more organizations are reporting cases of direct deposit fraud or near-misses. This article will provide you with some tips on how to recognize payroll direct deposit scam emails, particularly as they increase through the holiday season.
What is Business Email Compromise?
Imagine you receive an email requesting an urgent change to direct deposit information. If you or another administrator changes account numbers, multiple pay periods could pass before the individual realizes either part or all of their paycheck has been diverted into an alternate account.
The above is an example of business email compromise, where the individual whose paycheck was diverted never really requested the change. Instead, the change was requested by a bad actor impersonating the individual.
“Business email compromise is a serious threat targeting payroll operations, and it’s important for people to remain vigilant as perpetrators continually change their skills and tactics,” says Liz Boyer, Risk Mitigation Officer at Checkwriters. “For example, recent reports – like this one from cybersecurity provider Fortra – show that criminals are now using generative AI to create more deceptive emails to target victims. It’s easier than ever for fraudsters to pull off these attacks.”
Tips to Prevent Business Email Compromise
What can you do about it? This is where everyone in the organization plays the role of human firewall!
- Always treat requests for money or sensitive information with a high degree of skepticism.
- Slow down and think critically.
- Verbally confirm with the sender that the request is legitimate (verbally is the key word – if you respond to the email asking for confirmation, you’re likely responding directly to the scammer).
- Never assume a request is legitimate even if it comes from someone within your organization. Stay alert for anything out of the ordinary, and if you need more information, just ask!
Policies to Prevent Business Email Compromise
This also highlights the importance of maintaining strict policies when it comes to the personal financial information of employees.
- Direct Deposit account changes should only occur after a Direct Deposit Authorization Form is completed and signed, and, ideally, following a verbal confirmation of the requested change.
- Some organizations use the “four eyes principle” which requires two different people to sign off on major transactions.
“BEC is sophisticated because it avoids the use of malicious programs. Instead, it uses the victim’s trust to trick them into making fraudulent transactions,” says Youssef Karami, Director of IT Infrastructure at Checkwriters.
How to identify a fraudulent email
There are several tell-tale signs that the email you’re looking at is suspicious, and that the sender is attempting to commit direct deposit fraud.
Victims often report that it was “obvious” the request was a payroll direct deposit scam once they looked back at the email. Of course, hindsight is 20/20, and what matters is that payroll and HR professionals are on the lookout for red flags before any action is taken.
Some things to look out for include mismatched names and emails, a sense of urgency to the request, signature issues, and lack of a voided check or bank form.
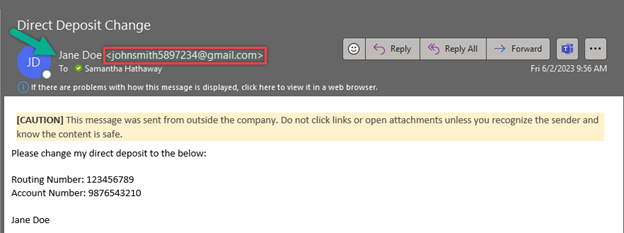
From Name and Email Address Mismatch
Check out the screenshot below. If the “From Name” does not match the email address, it’s a red flag and should raise immediate concerns about the authenticity of the request.
Sense Of Urgency
Fraudulent payroll direct deposit change requests are often marked by phrases like “this is urgent” or “please change my direct deposit immediately.”
This should raise the question, “what’s the rush?” Of course, urgent payroll requests exist, but fraudsters deliberately try to speed up the process. Any request containing these or similar words or phrases should raise a red flag.
Issues With the Signature
If the direct deposit change request includes a form attachment, look at the signature. While electronic signatures are very common, they should be viewed with suspicion until the request is verified.
Also, sloppy errors like spelling mistakes or the first and last name in reverse order are red flags (see example below).

No Voided Check
It’s highly recommended to require a voided check or bank encoding form with a payroll direct deposit change request. If these are not included – as in the example below – then you should be suspicious of the request. These inclusions allow you to verify the address and/or name on the check or bank encoding form match the employee’s demographics.
Similarly, you should pay close attention to the SSN provided and verify that with the information you have on record.

Mismatched email domains
If the email claims to be from a reputable company, like Microsoft or your bank, but the email is being sent from another email domain like gmail.com, or microsoftsupport.ru it’s probably a scam. Also be watchful for very subtle misspellings of the legitimate domain name. Like micros0ft.com where the second “o” has been replaced by a 0, or rnicrosoft.com, where the “m” has been replaced by an “r” and a “n”. These are common tricks of scammers.
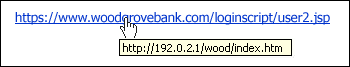
Suspicious links or unexpected attachments
If you suspect that an email message is a scam, don’t open any links or attachments that you see. Instead, hover your mouse over, but don’t click, the link to see if the address matches the link that was typed in the message. In the following example, resting the mouse over the link reveals the real web address in the box with the yellow background. Note that the string of numbers looks nothing like the company’s web address.
Conclusion
Payroll direct deposit scams are very common, and organizations across all industries have reported being targeted.
Payroll and HR professionals should always be suspicious of change requests until these requests are verified. You can do this through a phone conversation, face-to-face, or through another trusted, secondary form of communication.
In the meantime, pay close attention to the “red flag” items covered in this article, as they’ll serve as a first line of defense against those targeting you and your employees.
Here is an additional resource from Microsoft on protecting yourself from phishing.
Disclaimer: The information contained herein is not intended to be construed as legal advice, nor should it be relied on as such. Employers should closely monitor the rules and regulations specific to their jurisdiction(s) and should seek advice from counsel relative to their rights and responsibilities.